Roxana Ionescu and Oxana Gorgan
In celebration of the European Cybersecurity Month, we dedicate this article to the analysis of the reform of one of central EU legislation on cybersecurity – the Network and Information Security Directive (“NIS Directive”). For those unfamiliar, the NIS Directive is the first piece of EU legislation on cybersecurity, meant to establish a common level of security for network and information systems by addressing the threats posed to those systems that play a vital role in the society.
Essentially, the Directive established three strategies for ‘achieving a high common level of security of network and information systems’[1]:
- it created national capabilities for the Member States (they must have a national CSIRT (Directoratul National de Securitate Cibernetica in Romania);
- offered support for cooperation and information exchange among Member States (EU CSIRT network, NIS Cooperation Group); and
- lastly, it imposed national supervision of the cybersecurity of critical market operators[2], which in turn would have to take appropriate and proportionate technical and organisational measures to manage the risks posed to their security.
By 2020, all Member States had communicated to the Commission that they had fully transposed the directive into their national legislation.
1.The revision. Why proposing a revised Directive after less than a year after its transposition?
On 16 December 2020, the EU Commission published its proposal for a revised Directive on Security of Network and Information Systems, known as the NIS2 Directive.
This proposal comes in response to the growing threats posed by digitalization and the surge in cyber-attacks, which are both growing in scale, cost and sophistication. To illustrate, it was estimated an increase of 57x in global ransomware damage costs this year, compared to the ones in 2015. This means a company suffers a ransomware attack every 11 seconds.[3]
Another possible reason worth mentioning is also EU`s ambition to achieve more technological sovereignty in critical technologies, such as 5G, and define global standards and increase investment in technologies such as blockchain, high-performance and quantum computing. Naturally, this has to be complemented with a strengthened common cybersecurity policy.[4]
Thus, when the Commission carried an analysis to see how the NIS Directive is prepared for such risks and ambitions, it concluded that its scope was too limited in terms of the sectors covered, mainly due to increased digitalization in recent years. This made the scope of the NIS Directive insufficient by reference to all the digitalized sectors providing key services to the economy and society as a whole.
Other problems identified were:
- the lack of clarity as regards the scope criteria for OESs or the national competence over digital service providers,
- the implementation of the Directive in the national law in significantly different ways, creating additional burden for companies operating in more than one Member State, and
- the inefficiency of the supervision and enforcement regime.
2. What is changing?
The revised directive brings changes in all the three strategies described above.
2.1. Improved cooperation
One of the novelties brought by NIS2 in this area is the establishment of an EUCyber Crises Liaison Organisation Network (EU-CyCLONe) to support the coordinated management of EU-wide cybersecurity incidents, as well as to ensure the regular exchange of information.
NIS2 also comes with new responsibilities for the Member States to adopt a plan and designate national competent authorities responsible for participating in the response to cybersecurity incidents and crises at the EU level and strengthens the decisional role of the NIS Cooperation Group.
2.2 Expansion of the sectors covered
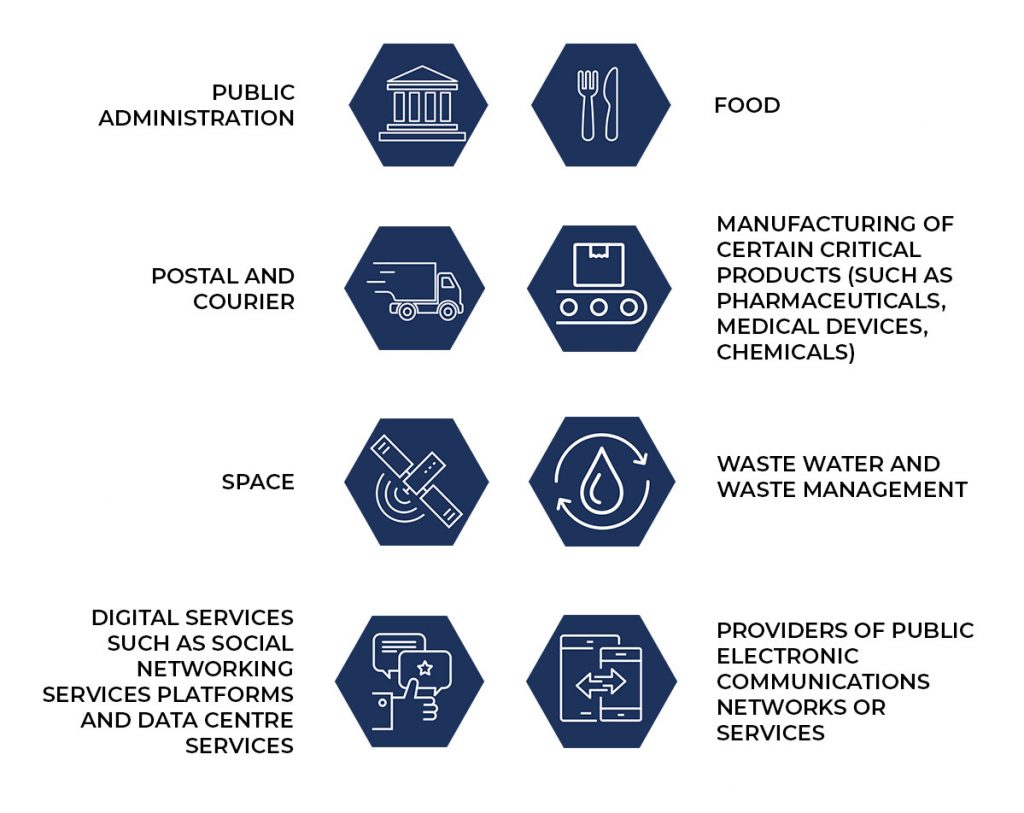
Perhaps the most important change brought by the NIS2 Directive is the significant extension of the scope by adding new sectors. Thus, in addition to the sectors already covered by the NIS Directive – healthcare, transport, banking and financial market infrastructure, digital infrastructure, water supply, energy, digital service providers, NIS2 includes the following sectors as either essential or important entities: public administration, food, postal and courier services, manufacturing of certain critical products (e.g. pharmaceuticals, medical devices, chemicals), space, waste water and waste management, space, digital services (e.g. social networking services platforms and data centre services), providers of public electronic communications network or services.[5]
Source: digital-strategy.ec.europa.eu
This means that such essential and important entities shall take technical and organisational measures to manage the risks posed to the security of network and information systems used, such asrisk analysis, incident handling, supply chain security, policies and procedures (testing and auditing), using cryptography and encryption. They would also have reporting obligations in regards to any significant impact on the provision of their services and take responsibility for the non-compliance with the obligations under the Directive.
You may have also observed the elimination of the OES and DSP distinction, replaced by essential and important entities. The distinction between the latter is made based on their importance, with consequences on the supervisory regime applicable: ex ante supervision for essential entities, and an ex post supervision of the important entities.
It is important to note, however, that micro and small entities are still excluded from the scope of the Directive. Nonetheless, if they indicate a key role for the economies or societies of Member States or for particular sectors or types of services (e.g. trust service providers, public administration), they are still covered by the Directive, irrespective of their size.[6]
To give an image to the amplitude of this change, it is estimated that approx. 100.000 companies are envisioned to be effected by this reform (in Germany, 45.000 companies, compared to 4500 covered by NIS1). No statistics are yet available for Romania, but it is reasonable to assume a similar range of impact.
- Stricter supervision and enforcement
NIS2 strengthens the power of national authorities and imposes stricter enforcement requirements. For example, the authorities would have the power to subject essential entities to on-site inspection and off site supervision, including random checks, regular audits, requests to access data, documents or any information necessary for the performance of their supervisory tasks etc.
In regards to incident reporting, the proposal sets a two-stage approach. First, affected companies would have 24 hours from when they first become aware of an incident to submit an initial report, followed by a final report no later than one month later.
Finally, Member States are obliged to impose significant administrative fines whenever entities breach the rules regarding cybersecurity risk management or reporting obligations of up to EUR 10,000,000 or 2 % of the total worldwide annual turnover of the undertaking to which the essential or important entity belongs in the preceding financial year, whichever is higher, penalties that one could say are inspired by the GDPR.
3. Concerns in different sectors
During the Open Public Consultation that ended on 18 March 2021, the general opinion was that the revision of the Directive is much welcomed. However, there were some common concerns expressed by representatives of various sectors, such as:
- The lack of a harmonized approach, which results in significant fragmentation in transposition across the EU. This comes across as problematic, especially for entities carrying activities in more than one Member State. Given that the proposal was still published in the form of a directive, this concern was still not addressed. There were also many organizations calling for alignment with the rest of EU law applicable
- Fear of over-reporting and calls for the extension of the incident notification from 24 hours to 72 hours, which would allow the business to prioritize the rectification of the problem and the restoration of the service in a timely manner
- The one size fits all approach is not realistic
- The penalties, which some even went as far as to call them ‘draconian’, do not reflect a collaborative approach and are disproportional
4. When would these changes become applicable?
The proposal for NIS2 is still under negotiations between the co-legislators, notably the Council of the EU and the European Parliament. Once the proposal is agreed and consequently adopted, Member States will have to transpose the NIS2 Directive within 18 months.
Conclusion
There is no doubt that the revised Network and Information Security Directive will bring significant improvements and represents a good step in making the EU fit for the digital age. However, there is also the certainty that it will oblige many companies to take major organizational and operational changes to be in conformity with the new dispositions. That is why we advise the entities active in sectors covered by the NIS2 to keep a close eye on the updates of this proposal, evaluate the applicability of the Directive to their activity and start taking a set of cybersecurity measures to ensure their conformity with the law.
[1] Art. 1 Directive (EU) 2016/1148 of the European Parliament and of the Council of 6 July 2016 concerning measures for a high common level of security of network and information systems across the Union (NIS Directive)
[2] The European Union Agency for Cybersecurity (ENISA), “NIS Directive.” , 2016, https://www.enisa.europa.eu/topics/nis-directive
[3] European Parliament, BRIEFING EU Legislation in Progress. The NIS2 Directive – a High Common Level of Cybersecurity in the EU (February 2021) <https://www.europarl.europa.eu/RegData/etudes/BRIE/2021/689333/EPRS_BRI(2021)689333_EN.pdf>.
[4] European Parliament, Legislative Train Schedule <https://www.europarl.europa.eu/legislative-train/theme-a-europe-fit-for-the-digital-age/fiche>.
[5] For a complete list and division between essential and important entities, see Annex I to the Proposal for a Directive of the European Parliament and of the Council on measures for a high common level of cybersecurity across the Union, repealing Directive 2016/1148
[6] Art. 2 of the Proposal for a Directive of the European Parliament and of the Council on measures for a high common level of cybersecurity across the Union, repealing Directive (EU) 2016/1148